SEDONA SAFEGUARD COMPLIANCE & VULNERABILITY MANAGEMENT
Safeguard Compliance & Vulnerability Management identifies and mitigates security vulnerabilities while ensuring regulatory compliant defenses.
PROACTIVE THREAT
ALERTING
Automates monitoring for compromised data, enhancing IT staff’s threat response.
TRACKING OF
COMPROMISED DATA
Streamlines incident response, aiding IT in
risk management.
ENHANCED INFRASTRUCTURE SECURITY
Identifies vulnerabilities, bolstering IT’s approach to third-party risks.
ABOUT SAFEGUARD CVM
Safeguard Compliance & Vulnerability Management (CVM) is a suite of features designed to fortify cyber defenses and ensure regulatory compliance. Included are essential components such as external scans for vulnerabilities and rapid deployment via SaaS or API integration. With features like dark web monitoring, automated SSL checks, compliance monitoring, and vulnerability scanning ensure strong protection while meeting compliance regulations.
LEARN MORE ABOUT CVM
For more detailed product information including a complete list of features, download this product's datasheet.
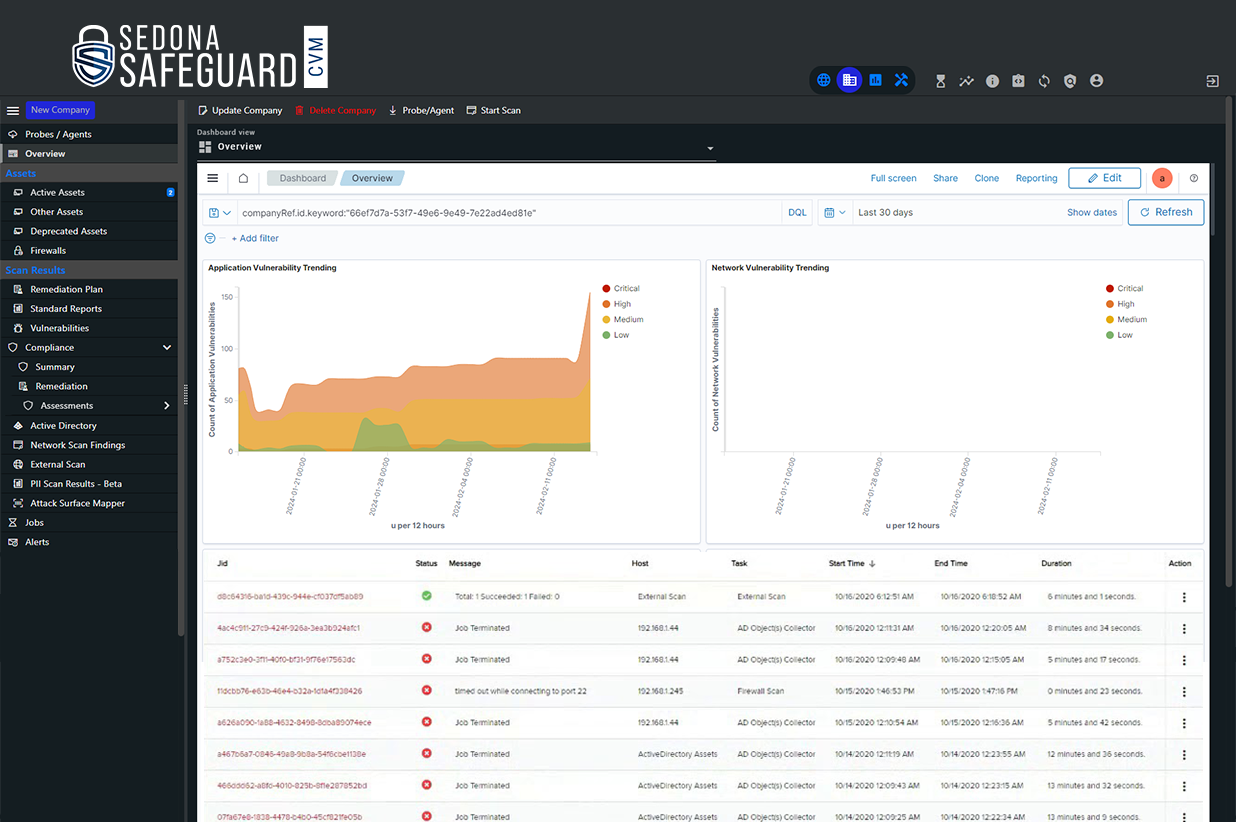
key features
24/7 DARK WEB MONITORING
Continuous serveillance of diverse platforms for comprehensive threat intelligence.
CYBER EDUCATION & AWARENESS
Enhances security posture through informed policy enforcement.
AUTOMATED ALERT SYSTEM
Delivers timely alerts on compromised data, enabling quick response and remediation.
INCIDENT RESPONSE WORKFLOW
Facilitates efficient handling and reporting of security incidents.
HOLISTIC THREAT INTELLIGENCE
Offers a broad view of security posturing, effectively strengthening cyber hygiene.
SUPPLY CHAIN RISK MANAGEMENT
Provides insights into supply chain vulnerabilities, improving third-party risk management.


